Imagine you’re handing out keys to your house. You wouldn’t give a spare key to every single person you know, right? Instead, you’d give keys only to those who absolutely need them—like your family or a trusted neighbor. This way, you minimize the risk of someone misusing access to your home. In the digital world, this concept is called the Least Privilege Principle, and it’s one of the most important rules for keeping your systems and data secure.
In this blog, we’ll break down what the Least Privilege Principle is, why it matters, and how it works in practice. We’ll also show you how solutions like Seamfix iAM can help you implement this principle effortlessly. Whether you’re an IT pro or just someone curious about cybersecurity, this guide will make the concept easy to understand—and maybe even a little fun!
What is the Least Privilege Principle?
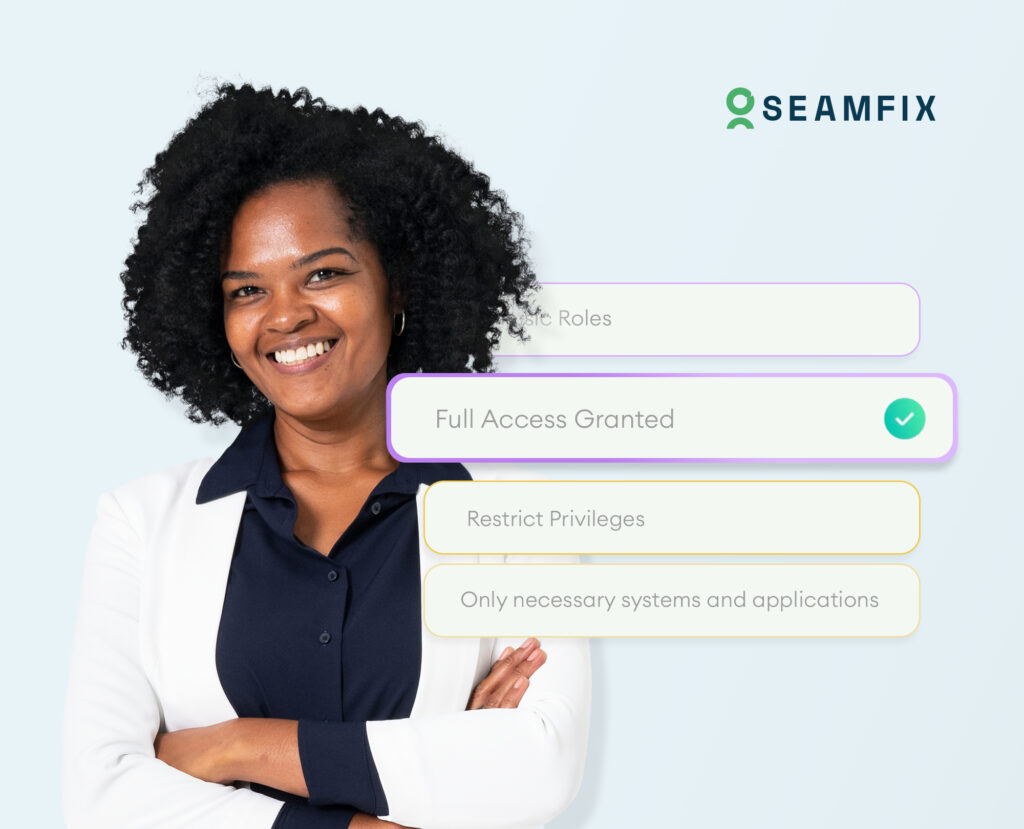
The Least Privilege Principle is a cybersecurity concept that means giving users the minimum level of access—or permissions—they need to do their jobs. Nothing more, nothing less. It’s like saying, “You only get the keys to the rooms you actually need to enter.”
For example:
- A marketing intern doesn’t need access to the company’s financial records.
- A developer doesn’t need access to HR systems.
- A customer support agent doesn’t need admin rights to the company’s servers.
By limiting access to only what’s necessary, you reduce the risk of accidental mistakes, insider threats, and external attacks.
Why the Least Privilege Principle Matters
So, why should you care about the Least Privilege Principle? Here are a few reasons:
- Reduces the Risk of Data Breaches: If a hacker compromises an account with limited access, they can’t do much damage.
- Prevents Insider Threats: Even well-meaning employees can accidentally cause harm if they have too much access.
- Improves Compliance: Many regulations (like GDPR, HIPAA, and PCI DSS) require organizations to follow the Least Privilege Principle.
- Simplifies Auditing: When users have only the access they need, it’s easier to track who’s doing what.
How the Least Privilege Principle Works in Practice
Implementing the Least Privilege Principle doesn’t have to be complicated. Here’s how it works in real life:
- Identify User Roles: Start by defining the roles in your organization (e.g., Manager, Developer, Intern).
- Assign Minimum Permissions: Give each role only the permissions they need to do their job. For example, a Developer might need access to code repositories but not to financial systems.
- Review and Adjust: Regularly review user permissions to ensure they’re still appropriate. If someone’s role changes, update their access accordingly.
- Monitor Access: Keep an eye on who’s accessing what. If something seems off, investigate.
Real-World Examples of the Least Privilege Principle
Still not convinced? Here are some real-world examples of how the Least Privilege Principle can make a difference:
1. Protecting Sensitive Data
- In a healthcare organization, only doctors and nurses should have access to patient records. Administrative staff, like receptionists, don’t need this access—so they shouldn’t have it.
2. Preventing Accidental Mistakes
- A marketing intern doesn’t need access to the company’s financial systems. If they accidentally delete or modify something, it could cause major problems.
3. Stopping Insider Threats
- If an employee leaves the company on bad terms, having limited access means they can’t take sensitive data with them or cause damage on their way out.
4. Meeting Compliance Requirements
- Many industries have regulations that require strict control over access to sensitive data. The Least Privilege Principle helps you meet these requirements.
How Seamfix iAM Supports the Least Privilege Principle
Now, let’s talk about how Seamfix iAM can help. Seamfix iAM is a modern Identity and Access Management (IAM) solution that makes it easy to implement the Least Privilege Principle. Here’s why it’s a great choice:
- Role-Based Access Control (RBAC): Seamfix iAM lets you define roles and assign permissions based on those roles. This makes it easy to ensure that users have only the access they need.
- Granular Permissions: With Seamfix iAM, you can set very specific permissions for each role, giving you fine-tuned control over access.
- Automated Provisioning and Deprovisioning: When a user’s role changes, Seamfix iAM automatically updates their permissions. This ensures that they always have the right level of access.
- User-Friendly: Seamfix iAM is designed with the end-user in mind. It’s easy to set up and use, even for non-tech-savvy employees.
For example, imagine you’re onboarding a new employee. With Seamfix iAM, you can assign them a role (e.g., “Sales Representative”) and they’ll automatically get the permissions they need—and nothing more. It’s the Least Privilege Principle made simple.
Tips for Implementing the Least Privilege Principle
Here are some tips to help you get the most out of the Least Privilege Principle:
- Start with a Plan: Identify the roles and permissions needed in your organization.
- Involve Key Stakeholders: Get input from IT, HR, and other relevant teams to ensure everyone’s needs are met.
- Communicate with Users: Let employees know why the Least Privilege Principle is being implemented and how it will benefit them.
- Monitor and Optimize: Keep an eye on how the system is performing and make adjustments as needed.
Final Thoughts
The Least Privilege Principle is one of the simplest yet most effective ways to improve your organization’s security. By giving users only the access they need, you can reduce the risk of data breaches, prevent insider threats, and meet compliance requirements.
And with solutions like Seamfix iAM, implementing the Least Privilege Principle has never been easier. It’s designed to make the process seamless, scalable, and user-friendly—so you can focus on what really matters: running your business.
So, what are you waiting for? Take the first step toward better security by exploring how Seamfix iAM can help.
Ready to learn more? Check out Seamfix iAM and its access control capabilities here.