In today’s digital world, where everything from your morning coffee order to your bank transactions happens online, managing who has access to what has become more critical than ever. Enter Identity and Access Management (IAM), the unsung hero of cybersecurity. But as technology evolves, so does IAM. One of the most exciting trends in this space is Identity as a Service (IDaaS). If you’re wondering what that means, don’t worry—we’re breaking it down in a way that’s easy to understand, friendly, and maybe even a little fun.
What is IAM, and Why Should You Care?
Let’s start with the basics. IAM, or Identity and Access Management, is like the bouncer at the door of a club. It ensures that only the right people get in and that they only have access to the areas they’re supposed to. In the digital world, this means managing user identities (like employees, customers, or partners) and controlling what systems, apps, or data they can access.
But here’s the thing: as businesses grow and technology becomes more complex, traditional IAM systems can feel like trying to manage a stadium-sized crowd with a single bouncer. That’s where Identity as a Service (IDaaS) comes in.
What is Identity as a Service (IDaaS)?
Imagine if that bouncer didn’t just work at one club but could manage access for every venue in the city, all while learning and adapting to new security threats. That’s essentially what IDaaS does. It’s a cloud-based solution that handles identity and access management without the need for on-premise hardware or software. Think of it as IAM, but smarter, faster, and more flexible.
IDaaS providers offer services like:
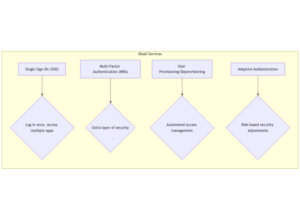
- Single Sign-On (SSO): Log in once, and you’re good to go across multiple apps.
- Multi-Factor Authentication (MFA): An extra layer of security to make sure it’s really you.
- User Provisioning and Deprovisioning: Automatically adding or removing access when someone joins or leaves an organization.
- Adaptive Authentication: Adjusting security measures based on risk levels (e.g., requiring MFA only for suspicious logins).
Why is IDaaS a Game-Changer?
- It’s Scalable: Whether you’re a small startup or a global enterprise, IDaaS grows with you. No need to worry about outgrowing your system.
- It’s Cost-Effective: Since it’s cloud-based, you don’t need to invest in expensive hardware or maintenance.
- It’s User-Friendly: Let’s face it—no one likes remembering 20 different passwords. IDaaS makes life easier for users while keeping things secure.
- It’s Future-Proof: With cyber threats evolving every day, IDaaS providers constantly update their systems to stay ahead of the curve.
Emerging Trends in IDaaS
The world of IDaaS is constantly evolving. Here are some of the hottest trends shaping its future:
- Zero Trust Security: The old model of “trust but verify” is out. Zero Trust means no one is trusted by default, not even inside the network. IDaaS plays a key role in enforcing this by continuously verifying identities and access.
- AI and Machine Learning: IDaaS platforms are getting smarter. They can detect unusual behavior (like logging in from a new device or location) and automatically tighten security.
- Passwordless Authentication: Passwords are so 2010. IDaaS is moving toward biometrics (like fingerprints or facial recognition) and other passwordless methods to make security seamless and user-friendly.
- Integration with IoT: As more devices get connected (think smart thermostats, wearables, etc.), IDaaS is stepping up to manage identities and access for the Internet of Things.
- Privacy and Compliance: With regulations like GDPR and CCPA, businesses need to ensure they’re handling user data responsibly. IDaaS helps by providing tools for compliance and data protection.
Where Does Seamfix iAM Fit In?
Now, let’s talk about a real-world example. Seamfix iAM is a cutting-edge IAM solution that embodies many of these emerging trends. Designed with scalability and user experience in mind, Seamfix iAM offers features like Single Sign-On, Multi-Factor Authentication, and seamless integration with existing systems. Whether you’re a business looking to streamline access for your employees or a service provider managing customer identities, Seamfix iAM makes it easy to stay secure without sacrificing convenience.
What sets Seamfix iAM apart is its focus on adaptability. In a world where cyber threats are constantly evolving, having a solution that can grow and adapt with your needs is crucial. Plus, its user-friendly design ensures that even non-tech-savvy users can navigate it with ease.
Why Should You Care About IDaaS?
If you’re a business owner, IT professional, or even just someone who uses the internet (so, everyone), IDaaS matters. It’s not just about keeping hackers out—it’s about creating a seamless, secure experience for everyone involved. Whether it’s protecting sensitive data, simplifying login processes, or ensuring compliance with regulations, IDaaS is the future of identity management.
And with solutions like Seamfix iAM leading the charge, adopting IDaaS has never been easier or more accessible.
Final Thoughts
The world of IAM is changing fast, and IDaaS is at the forefront of this transformation. It’s not just a trend—it’s a necessity in today’s digital landscape. By embracing IDaaS, businesses can stay secure, scalable, and ahead of the curve.
So, whether you’re exploring IAM solutions for the first time or looking to upgrade your current system, now’s the time to dive into the world of Identity as a Service. And who knows? With tools like Seamfix iAM, you might just find that managing identities is easier—and more exciting—than you ever imagined.
Ready to take the plunge? Learn more about how Seamfix iAM can transform your identity management strategy here.


