Understanding IAM Protocols and Standards
Imagine you’re the owner of a super-exclusive club. You’ve got VIPs, regular members, and staff, all needing different levels of access. You wouldn’t want just anyone walking into the VIP lounge, right? That’s where Understanding IAM Protocols and Standards comes in. Think of them as the bouncer, the guest list, and the keycard system all rolled into one, ensuring the right people get the right access at the right time.
In the digital world, IAM protocols and standards are the backbone of security and efficiency. They help organizations manage who has access to what, ensuring sensitive information stays safe while making life easier for users. Let’s break it down in a way that’s easy to understand, and we’ll even sprinkle in how Seamfix iAM (more on that later) fits into the picture.
What Are IAM Protocols and Standards?
IAM protocols and standards are the rules and frameworks that govern how identities (like users, devices, or applications) are authenticated, authorized, and managed within a system. Think of them as the “rulebook” for how your digital club operates. They ensure that only the right people get in, and once they’re in, they can only access what they’re supposed to.
Some of the most common IAM protocols and standards include:
- OAuth 2.0: This is like a digital handshake. It allows apps to access your information on another app without sharing your password. For example, when you log into a website using your Google account, OAuth 2.0 is working behind the scenes.
- OpenID Connect (OIDC): Built on top of OAuth 2.0, this protocol helps verify your identity. It’s like the bouncer checking your ID before letting you into the club.
- SAML (Security Assertion Markup Language): This is the protocol that lets you log in once and access multiple services without needing to log in again. It’s like having a VIP pass that gets you into all the rooms in the club.
- LDAP (Lightweight Directory Access Protocol): This is the directory that stores all the user information, like usernames, passwords, and permissions. It’s the guest list the bouncer checks before letting you in.
- SCIM (System for Cross-domain Identity Management): This standard helps manage user identities across different systems. It’s like updating the guest list across all the clubs in town at once.
Why Are IAM Protocols and Standards Important?
Without IAM protocols and standards, managing access to digital resources would be chaotic. Here’s why they matter:
- Security: They ensure that only authorized users can access sensitive information, reducing the risk of data breaches.
- Convenience: They make it easy for users to log in and access multiple services without remembering a million passwords.
- Compliance: Many industries have regulations that require strict control over who can access what. IAM protocols help organizations stay compliant.
- Efficiency: Automating user access management saves time and reduces errors.
How Does Seamfix iAM Fit Into All This?
Now that we’ve covered the basics, let’s talk about Seamfix iAM. Seamfix iAM is a robust Identity and Access Management solution designed to simplify and secure how organizations manage user identities and access. It’s like having a top-tier security team for your digital club, ensuring everything runs smoothly and securely.
Here’s how Seamfix iAM stands out:
- Seamless Integration: Seamfix iAM supports industry-standard protocols like OAuth 2.0, OpenID Connect, and SAML, making it easy to integrate with existing systems. Whether you’re using cloud-based apps or on-premise solutions, Seamfix iAM has got you covered.
- User-Friendly: With Seamfix iAM, managing user identities is a breeze. Its intuitive interface makes it easy to onboard new users, assign roles, and manage permissions—no tech degree required.
- Scalable: Whether you’re a small business or a large enterprise, Seamfix iAM grows with you. It’s designed to handle thousands of users without breaking a sweat.
- Secure: Security is at the heart of Seamfix iAM. It uses advanced encryption and authentication methods to ensure your data stays safe.
- Compliance Ready: Seamfix iAM helps you meet regulatory requirements by providing detailed audit trails and access controls.
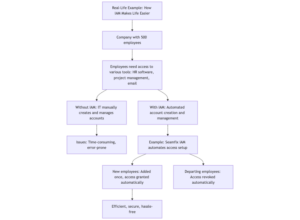
Real-Life Example: How IAM Makes Life Easier
Let’s say you work at a company with 500 employees. Each employee needs access to different tools and systems—HR software, project management tools, email, and more. Without IAM, the IT team would have to manually create and manage accounts for each employee, which is time-consuming and prone to errors.
With IAM protocols and a solution like Seamfix iAM, the process is automated. When a new employee joins, they’re added to the system once, and their access to all the tools they need is automatically set up. If they leave, their access is revoked just as easily. It’s efficient, secure, and hassle-free.
The Future of IAM
As technology evolves, so do IAM protocols and standards. We’re seeing trends like:
- Passwordless Authentication: Using biometrics (like fingerprints or facial recognition) or hardware tokens instead of passwords.
- Zero Trust Security: A model where no one is trusted by default, even if they’re inside the network. Every access request is verified.
- AI-Driven IAM: Using artificial intelligence to detect unusual behavior and prevent unauthorized access.
Solutions like Seamfix iAM are already incorporating these advancements, ensuring they stay ahead of the curve.
Final Thought
IAM protocols and standards might sound technical, but they’re really about making our digital lives safer and easier. They’re the invisible guardians that keep our data secure while ensuring we can access what we need without jumping through hoops.
And when it comes to implementing IAM, Seamfix iAM is a standout choice. It’s secure, scalable, and user-friendly, making it a great fit for businesses of all sizes. Whether you’re just starting to explore IAM or looking to upgrade your current system, Seamfix iAM is worth checking out.
So, the next time you log into your favorite app with a single click, remember the IAM protocols working behind the scenes—and maybe give a little nod to solutions like Seamfix iAM that make it all possible.
Ready to take your IAM game to the next level? Learn more about Seamfix iAM here and see how it can transform the way you manage identities and access.









