What is MFA?
Imagine your front door has not one, but two locks. Even if someone picks the first lock, they’re stuck unless they have the second key. That’s Multi-Factor Authentication (MFA) in action!
MFA is a security process that requires you to prove your identity in two or more ways before you can access your account. Instead of just relying on a password, you need to provide additional proof that you’re really you.
Here’s how it breaks down:
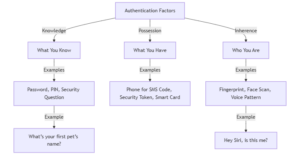
- What You Know:
- Your password, PIN, or the answer to a security question. “What’s your first pet’s name?”
- What You Have:
- Your phone (for a text code), a security token, or a smart card.
- Who You Are:
- Biometric data like your fingerprint, face scan, or voice pattern. “Hey Siri, is this me?”
By combining at least two of these factors, MFA makes it way harder for hackers to break in.
Why is MFA Important?
Let’s face it: passwords are kind of like flimsy locks. They’re easy to guess, steal, or hack. MFA is like adding a security system, a guard dog, and a moat around your digital life. Here’s why it’s a game-changer:
- Stops Password-Based Attacks:
- Even if a hacker steals your password, they’re stuck without the second factor. No second key, no entry.
- Reduces Phishing Risks:
- If someone tricks you into giving up your password, they still can’t get in without the second factor. Take that, scammers!
- Keeps You Compliant:
- Many industries require MFA to meet security regulations. It’s not just smart; it’s the law.
- Protects Remote Work:
- With more people working from home, MFA ensures only authorized users can access company resources. No more “Oops, I left my laptop at the coffee shop” disasters.
How to Implement MFA Like a Pro
Ready to level up your security? Here’s how to roll out MFA without breaking a sweat:
1. Choose the Right MFA Methods
Not all MFA methods are created equal. Here are some popular options:
- SMS/Email Codes: A one-time password (OTP) sent to your phone or email. Simple but effective.
- Authenticator Apps: Apps like Google Authenticator or Microsoft Authenticator generate time-based codes. No signal? No problem.
- Biometric Authentication: Use your fingerprint, face, or voice to prove it’s you. Futuristic and fun.
- Hardware Tokens: Physical keys like YubiKey that you plug into your device. Old-school cool.
2. Use Adaptive MFA
This is like having a security system that thinks. Adaptive MFA evaluates your behavior and risk level before deciding how many factors to require. For example:
- If you log in from your usual device and location, it might just ask for a password.
- If you log in from a new device or a different country, it’ll ask for extra verification. “Hey, is this really you?”
3. Educate Your Users
Even the best MFA system won’t work if people don’t understand it. Here’s how to get everyone on board:
- Train employees to spot phishing attempts. “That email from ‘IT Support’ looks fishy…”
- Encourage strong, unique passwords. “Password123” is not your friend.
- Make security awareness part of everyday life. Because cyber hygiene is a thing.
Final Thoughts
MFA is like adding a seatbelt to your digital life. It’s simple, effective, and can save you from a world of hurt. Whether you’re a business protecting sensitive data or just someone who wants to keep their cat photos safe, enabling MFA is a no-brainer.
So, if you haven’t already turned on MFA for your accounts, what are you waiting for? It’s time to suit up with your digital superhero cape and keep the bad guys out. Seamfix iAM makes it easy to implement secure access controls, ensuring your organization stays protected with seamless and scalable identity management.









