Imagine your organization is a fortress. You’ve got thick walls, a moat, and guards at every entrance. But what if someone inside the fortress accidentally left a door unlocked? Or worse, what if a guard handed over the keys to a stranger? That’s where Identity and Access Management (IAM) comes in. It’s the digital bodyguard that ensures only the right people have access to your fortress—and keeps the bad guys out.
In this article, we’ll explore the role of IAM in cybersecurity, breaking it down into simple, easy-to-understand terms. We’ll also touch on how tools like Seamfix iAM can help you strengthen your cybersecurity defenses. Let’s dive in!
What is IAM, and Why is it Critical for Cybersecurity?
Identity and Access Management (IAM) is a framework that ensures the right people have the right access to the right resources at the right time. In the context of cybersecurity, IAM is your first line of defense against unauthorized access, data breaches, and cyberattacks.
Think of IAM as the gatekeeper of your digital fortress. It verifies who’s trying to enter (authentication), decides what they’re allowed to do (authorization), and keeps a record of their activities (auditing). Without IAM, your organization is like a fortress with no guards—wide open to threats.
How IAM Strengthens Cyber security
Let’s break down the key ways IAM plays a critical role in cybersecurity:
1. Preventing Unauthorized Access
- Authentication: IAM ensures that only legitimate users can access your systems. This often involves multi-factor authentication (MFA), which requires users to provide two or more forms of verification (e.g., a password and a fingerprint).
- Example: Without IAM, a hacker could easily guess a weak password and gain access to sensitive data. With IAM, even if they guess the password, they’d still need a second form of verification to get in.
2. Enforcing Least Privilege
- Authorization: IAM ensures users only have access to the resources they need to perform their tasks—nothing more, nothing less. This minimizes the risk of accidental or intentional misuse of sensitive data.
- Example: An employee in the marketing department doesn’t need access to financial records. IAM ensures they can’t access those records, reducing the risk of a data breach.
3. Detecting and Responding to Threats
- Auditing: IAM keeps detailed logs of user activities, making it easier to detect and respond to suspicious behavior.
- Example: If an employee’s account is compromised and used to access sensitive data, IAM logs can help you identify the breach and take corrective action.
4. Simplifying Compliance
- Many cybersecurity regulations require organizations to enforce strict access controls and maintain detailed audit trails. IAM helps you meet these requirements with ease.
- Example: During an audit, IAM provides the documentation you need to demonstrate compliance with regulations like GDPR or HIPAA.
Real-World Cybersecurity Threats IAM Can Mitigate
Let’s look at some common cybersecurity threats and how IAM can help mitigate them:
1. Phishing Attacks
- Phishing attacks often involve tricking users into revealing their credentials. IAM mitigates this risk by requiring MFA, so even if a user’s password is compromised, the attacker still can’t gain access.
2. Insider Threats
- Insider threats—whether accidental or intentional—are a major cybersecurity risk. IAM minimizes this risk by enforcing least privilege and keeping detailed logs of user activities.
3. Brute Force Attacks
- Brute force attacks involve guessing passwords through trial and error. IAM mitigates this risk by locking accounts after multiple failed login attempts and requiring strong, complex passwords.
4. Data Breaches
- Data breaches often occur when unauthorized users gain access to sensitive data. IAM prevents this by ensuring only authorized users can access sensitive resources.
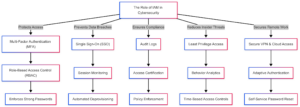
How Seamfix iAM Enhances Cybersecurity
Implementing IAM doesn’t have to be complicated. With the right tools, you can strengthen your cybersecurity defenses without the headache. That’s where Seamfix iAM comes in.
Seamfix iAM is an Identity and Access Management solution designed to simplify and secure access management. Here’s how it enhances cybersecurity:
- Strong Authentication: Supports MFA and other advanced authentication methods to keep your systems secure.
- Role-Based Access Control (RBAC): Ensures users only have access to the resources they need, minimizing the risk of insider threats.
- Audit Trails: Provides detailed logs of user activities, making it easy to detect and respond to suspicious behavior.
- Compliance Support: Helps you meet regulatory requirements with ease, reducing the risk of costly fines.
By leveraging Seamfix iAM, you can take the complexity out of IAM and focus on what really matters—keeping your organization secure.
Best Practices for Using IAM in Cybersecurity
Ready to get started with IAM? Here are some best practices to keep in mind:
- Implement Multi-Factor Authentication (MFA): MFA adds an extra layer of security, making it harder for attackers to gain access.
- Enforce Least Privilege: Only give users the access they need to perform their tasks—nothing more.
- Regularly Review Permissions: Periodically audit user access to ensure it’s still appropriate.
- Monitor and Audit: Keep detailed logs of user activities and review them regularly to detect and respond to threats.
Final Thoughts
In the world of cybersecurity, IAM is your digital bodyguard. It prevents unauthorized access, enforces least privilege, detects threats, and simplifies compliance. By implementing IAM, you can strengthen your organization’s cybersecurity defenses and protect your most valuable assets.
And if you’re looking for a tool to make IAM implementation easy and effective, Seamfix iAM is here to help. With its robust features, user-friendly interface, and seamless integration, Seamfix iAM takes the stress out of access management.
So, why wait? Start exploring IAM today and take the first step toward a more secure and resilient organization.
Curious to learn more about Seamfix iAM? Visit their website at https://seamfix.com/iam/ or reach out to their team for a demo. Your journey to better cybersecurity starts here!