What is Kerberos?
Imagine you’re trying to get into an exclusive club. You can’t just walk in; you need a special pass. But instead of a bouncer, there’s a super-smart system that checks your ID, gives you a temporary wristband, and lets you move around without showing your ID every 5 minutes. This is similar to Kerberos Authentication: How It Works in IAM, where a trusted system verifies your identity once and then allows you secure, ongoing access without needing to repeatedly authenticate.
That’s Kerberos Authentication: How It Works in IAM! It’s a secure authentication protocol that keeps your network safe by making sure only the right people (or systems) get access. And yes, it’s named after the three-headed dog from Greek mythology that guards the gates of the underworld. Appropriate, right?
How Does Kerberos Work?
Kerberos is like a VIP concierge for your network. Here’s how it rolls:
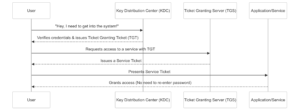
- You Ask for Access:
- You log in and say, “Hey, I need to get into the system!”
- The Key Distribution Center (KDC) Checks You Out:
- The KDC (the brains of the operation) verifies your credentials. If you’re legit, it gives you a Ticket Granting Ticket (TGT). Think of this as your backstage pass.
- You Request Access to a Service:
- Now you want to access something specific, like your email or a shared drive. You show your TGT to the Ticket Granting Server (TGS), which gives you a Service Ticket.
- You Get In:
- You present the Service Ticket to the app or service you’re trying to access. If everything checks out, you’re in! No more typing passwords a million times.
- You present the Service Ticket to the app or service you’re trying to access. If everything checks out, you’re in! No more typing passwords a million times.
Key Components of Kerberos Authentication
Let’s meet the crew:
- Key Distribution Center (KDC): The main hub that handles authentication and ticket distribution.
- Authentication Server (AS): The part of the KDC that checks your credentials and gives you the TGT.
- Ticket Granting Server (TGS): The part of the KDC that gives you Service Tickets for specific apps or services.
- Service Principal: The app or service you’re trying to access.
- Tickets: Encrypted passes that prove you’re allowed to be there.
Why Should You Care About Kerberos?
Here’s why Kerberos is a big deal:
- Strong Security:
- Uses encryption and timestamps to stop hackers from sneaking in. No replay attacks here!
- Single Sign-On (SSO):
- Log in once, access everything. No more password fatigue.
- Mutual Authentication:
- Both you and the service verify each other. It’s like a secret handshake.
- Scalability:
- Works for small teams or massive enterprises. Got 10 users or 10,000? Kerberos can handle it.
Common Use Cases for Kerberos
Here’s where Kerberos shines:
- Enterprise Network Authentication:
- Keeps corporate networks secure. No freeloaders allowed.
- Windows Active Directory:
- Microsoft uses Kerberos as the default authentication protocol. It’s the backbone of your Windows login.
- Secure Application Authentication:
- Used for databases, email servers, and other enterprise apps. Keeps your data safe and sound.
- Cloud and Hybrid IAM Implementations:
- Works in hybrid setups where some systems are on-premises and others are in the cloud. Best of both worlds.
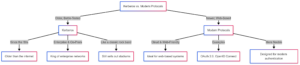
Kerberos vs. Modern Protocols
Kerberos has been around since the ’80s (yes, it’s older than the internet as we know it). While newer protocols like OAuth 2.0 and OpenID Connect (OIDC) are great for web-based systems, Kerberos is still the king of on-premises and enterprise networks. It’s like the classic rock band that still sells out stadiums.
Final Thoughts
Kerberos authentication might sound complicated, but at its core, it’s all about keeping your digital life secure and hassle-free. Whether you’re logging into your work computer, accessing a shared folder, or checking your email, Kerberos authentication is working behind the scenes to make sure only you get in.
So next time you hear “Kerberos,” think of it as your three-headed digital bodyguard—always on duty, always protecting your stuff. For organizations looking to streamline and secure their authentication processes, Seamfix iAM offers easy-to-implement IAM solutions.