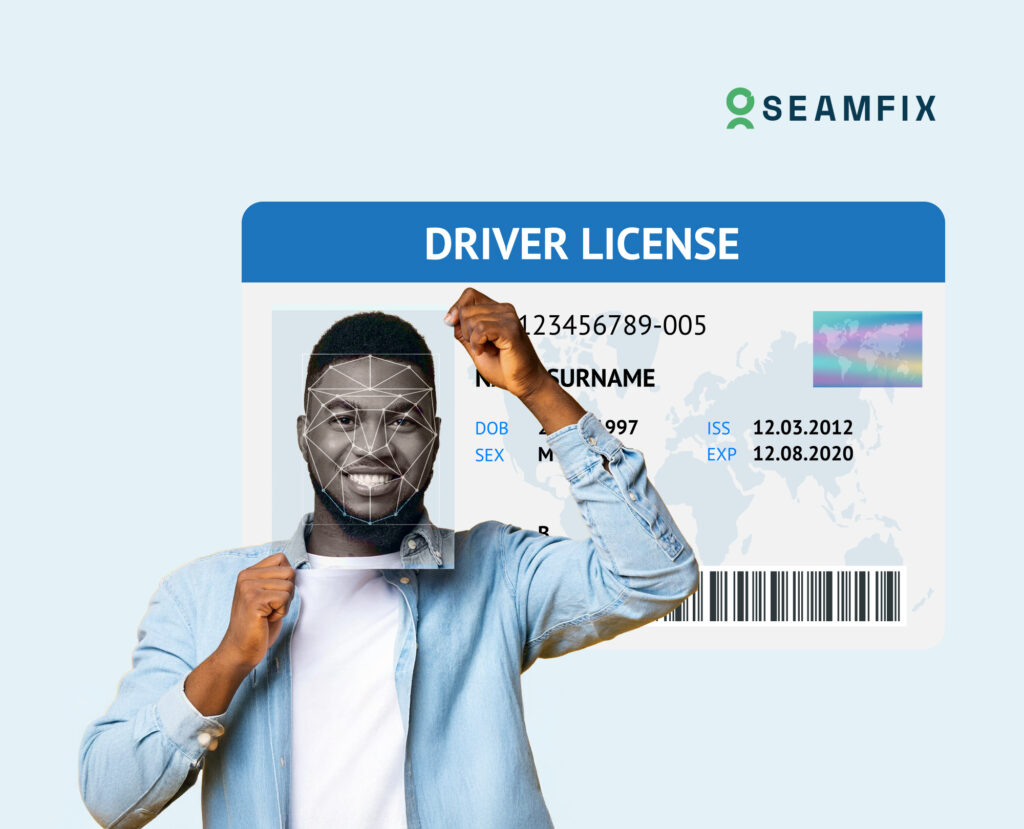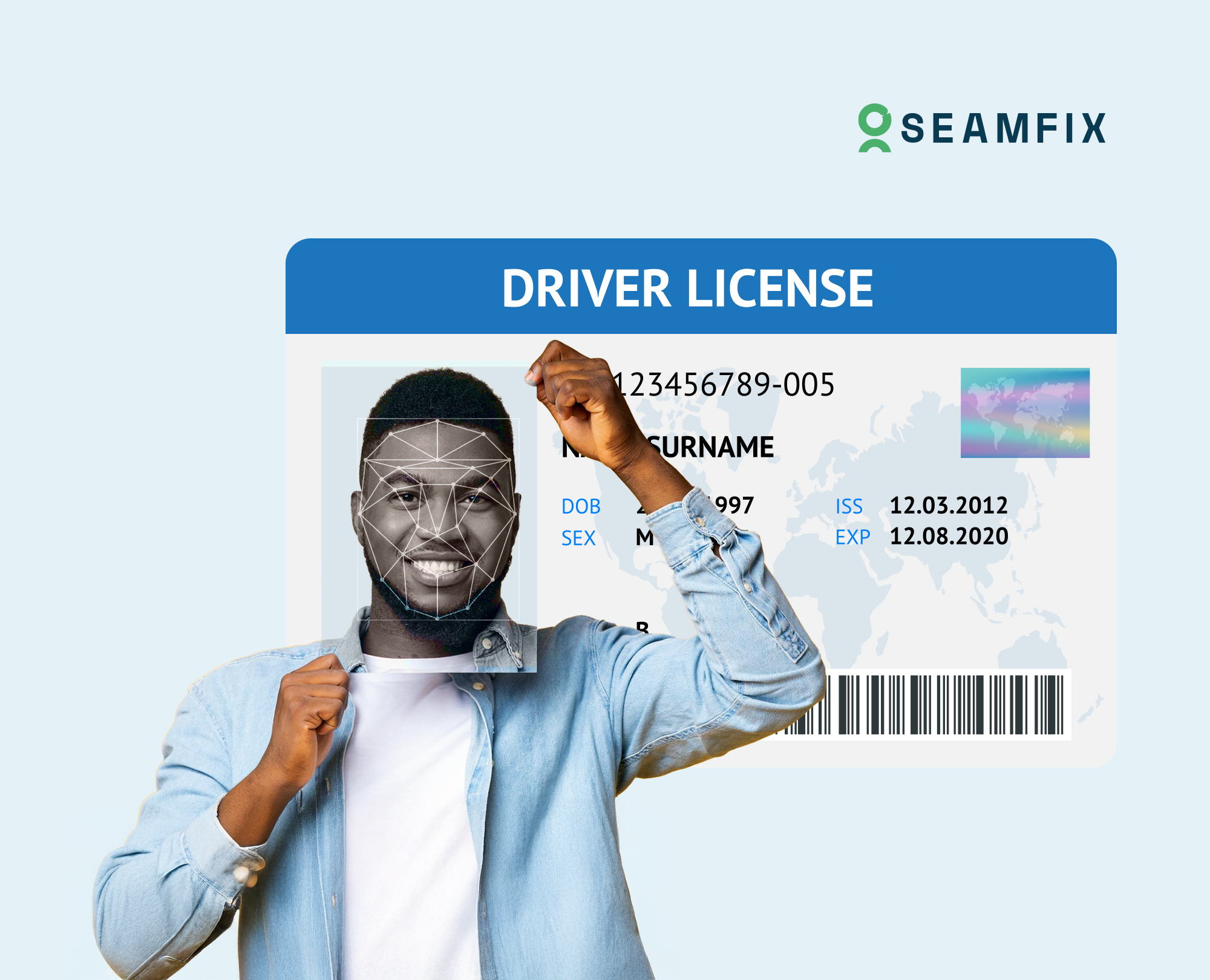
Reducing Fraud in ID Enrollment: What Liveness Detection Actually Catches
When someone shows up to get a SIM card, open a bank account, or get a government ID, the process is simple. They provide their personal information, their biometrics are captured and the application is processed. What Happens in Self Service Environments? Digital transformation is spreading across industries and