How Governments Use Digital Identity to Improve Service Delivery
Governments do not fail citizens because they lack intent. They fail when systems cannot answer a basic question. Who is this person and what are they entitled to receive? A public hospital delays treatment because staff cannot confirm eligibility. A social welfare office pays the same benefit twice to the same person. A passport office […]
Understanding Access Control and Why It Matters for Growing Organizations

The problem growth exposes A fast growing company hires fifty people in three months and gives new staff shared passwords so work can start on day one, while contractors keep access after projects end. Nothing breaks at first until payroll data leaks to the wrong inbox. It’s time for an audit and when an auditor […]
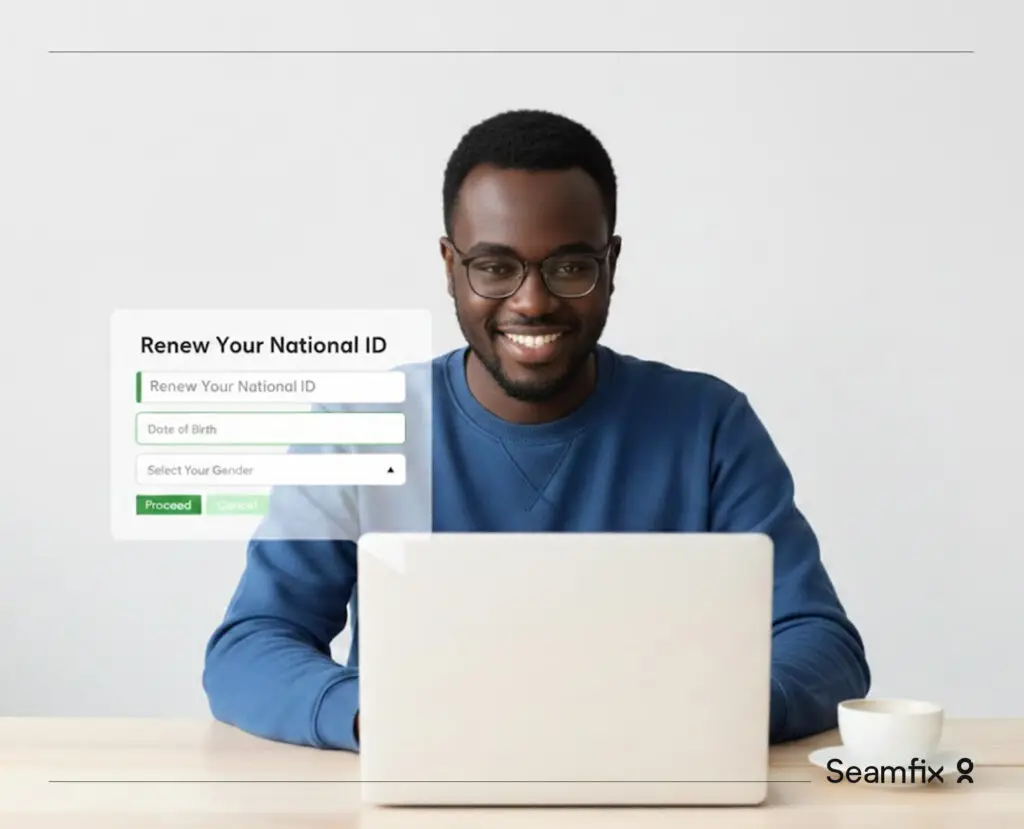
Seamfix Simplifies Passport Renewal for the Diaspora with ePass

For millions of citizens living outside their home countries, renewing an international passport can be stressful, expensive, and time-consuming. Long journeys to embassies, extended waiting times, and fragmented processes often turn a basic civic need into a major disruption. At Seamfix, we set out to change this reality. In collaboration with the Government of the […]
IAM for Mergers and Acquisitions: Best Practices

Mergers and acquisitions (M&A) are like corporate marriages. They’re exciting, full of potential, and can lead to incredible growth. But just like any marriage, they come with their fair share of challenges—especially when it comes to integrating two different systems, cultures, and processes. One of the biggest hurdles? Managing identities and access across the newly […]
Practical Guide for Implementing MFA for Organizations

Let’s talk about passwords for a second. We all know they’re important, but let’s be honest—they’re also kind of a pain. You have to remember them, change them regularly, and hope they’re strong enough to keep hackers out. But here’s the thing: passwords alone just aren’t enough anymore. That’s where Multi-Factor Authentication (MFA) comes in. […]
Building a Secure User Provisioning Process

In today’s digital world, building a secure user provisioning process is a critical task for any organization. Whether you’re a small business or a large enterprise, ensuring that the right people have the right access at the right time is essential for both productivity and security. But let’s be honest—user provisioning can sound like a […]
Custom Connector Support in IAM

Imagine you’re building a puzzle, but some of the pieces don’t quite fit. Frustrating, right? Now, think of your organization’s Identity and Access Management (IAM) system as that puzzle. You have all these different applications, systems, and tools, but they don’t always play nicely together. That’s where Custom Connector Support comes in—it’s like the magical […]
IAM for Mergers and Acquisitions: Best Practices

Mergers and acquisitions (M&A) are like corporate marriages. They’re exciting, full of potential, and can lead to incredible growth. But just like any marriage, they come with their fair share of challenges—especially when it comes to integrating two different systems, cultures, and processes. One of the biggest hurdles? Managing identities and access across the newly […]
Custom Connector Support in IAM

Imagine you’re building a puzzle, but some of the pieces don’t quite fit. Frustrating, right? Now, think of your organization’s Identity and Access Management (IAM) system as that puzzle. You have all these different applications, systems, and tools, but they don’t always play nicely together. That’s where Custom Connector Support comes in—it’s like the magical […]
Building a Secure User Provisioning Process

In today’s digital world, building a secure user provisioning process is a critical task for any organization. Whether you’re a small business or a large enterprise, ensuring that the right people have the right access at the right time is essential for both productivity and security. But let’s be honest—user provisioning can sound like a […]