Role-Based and Attribute-Based Access in IAM

Role-Based and Attribute-Based Access: A Beginner’s Guide to Role-Based Access Control (RBAC) Imagine you’re running a busy restaurant. You’ve got chefs in the kitchen, servers on the floor, and managers overseeing everything. Now, imagine if the chefs had access to the cash register, or the servers could change the menu. Chaos, right? That’s why you […]
Attribute-Based Access Control (ABAC): When and Why to Use It

Imagine you’re hosting a party. You’ve got a guest list, but instead of just checking names, you’re also looking at other factors: Are they wearing the right dress code? Did they RSVP? Are they arriving during the party hours? This extra layer of checks ensures that only the right people get in, at the right […]
Role Based vs. Attribute Based vs. Policy Based Access Control
Role Based vs. Attribute Based vs. Policy Based Access Control Imagine you’re running a theme park. You’ve got different zones—kiddie rides, thrill rides, and VIP lounges. Now, you need to decide who gets access to which areas. Do you give everyone a wristband based on their age (Role-Based Access Control) as part of your role-based-vs-attribute-based-vs-policy-based-access-control […]
The Least Privilege Principle in IAM
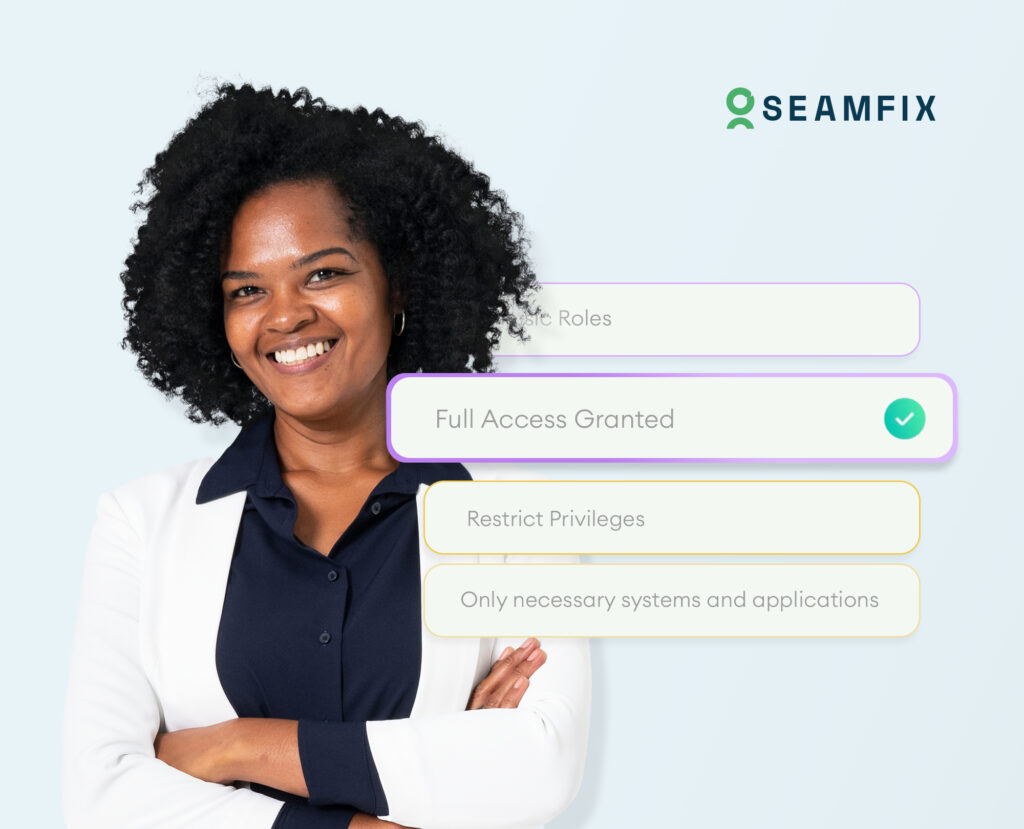
Imagine you’re handing out keys to your house. You wouldn’t give a spare key to every single person you know, right? Instead, you’d give keys only to those who absolutely need them—like your family or a trusted neighbor. This way, you minimize the risk of someone misusing access to your home. In the digital world, […]
Just-in-Time (JIT) Access in IAM

Imagine this: You’re hosting a party, and instead of giving everyone a key to your house, you only hand out keys to the people who need them, exactly when they need them. Sounds smart, right? That’s essentially what Just-in-Time (JIT) Access is all about in the world of Identity and Access Management (IAM). It’s a […]
User Lifecycle Management in IAM

Imagine running a ship. You’ve got a crew of talented people, each with their own roles and responsibilities. But what happens when someone new joins the crew? Or when someone leaves? Or when their role changes? If you don’t manage these transitions smoothly, things can get chaotic pretty quickly. That’s where User Lifecycle Management (ULM) […]
Dynamic access provisioning: Benefits and examples.

Ever feel like managing who gets access to what at work is like playing a never-ending game of “Simon Says”? Traditional access control methods can be clunky, time-consuming, and honestly, a bit of a headache. Think about it: manually adding and removing permissions every time someone joins, moves teams, or leaves the company? Tedious, right? […]
Group-Based Access Control: Simplifying Security Without the Headache

Let’s face it—managing user access in an organization can feel like herding cats. With so many users, roles, and permissions to keep track of, it’s easy to get overwhelmed. But what if there was a way to simplify the process, make it more efficient, and still keep your systems secure? Enter Group-Based Access Control (GBAC), […]
Group-Based Access Control: Simplifying Security Without the Headache

Let’s face it—managing user access in an organization can feel like herding cats. With so many users, roles, and permissions to keep track of, it’s easy to get overwhelmed. But what if there was a way to simplify the process, make it more efficient, and still keep your systems secure? Enter Group-Based Access Control (GBAC), […]
Dynamic access provisioning: Benefits and examples.

Ever feel like managing who gets access to what at work is like playing a never-ending game of “Simon Says”? Traditional access control methods can be clunky, time-consuming, and honestly, a bit of a headache. Think about it: manually adding and removing permissions every time someone joins, moves teams, or leaves the company? Tedious, right? […]